Table of contents
🎯𝐏𝐑𝐎𝐉𝐄𝐂𝐓 𝐎𝐕𝐄𝐑𝐕𝐈𝐄𝐖🌐
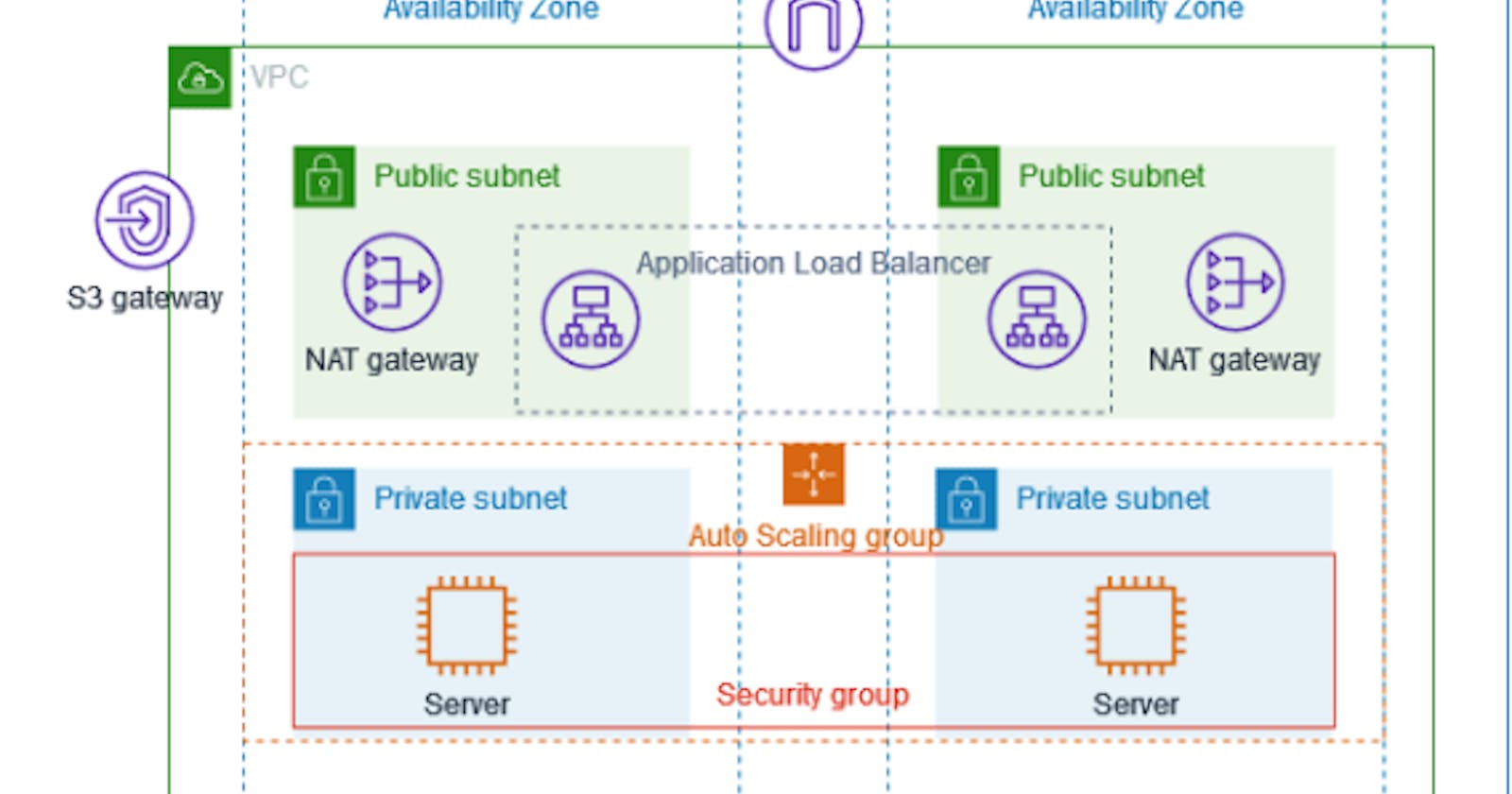
🔗𝐂𝐫𝐞𝐚𝐭𝐢𝐧𝐠 𝐚 𝐕𝐏𝐂
➤servers are deployed in two availability zones
➤Auto scaling groups
➤Application load balancer
➤There is one public and one private subnet in both the availability zones
➤For additional security we deploy servers on private subnets
➤Each public subnet contains NAT GATEWAY
➤uses SECURITY GROUPS for additional security
➤Jump-Host for masking the private subnet ec2 ip-address.
steps:
Create a Vpc by selecting vpc and more.

While creating the route tables see to it that you Allot 1 per AZ Nat Gateway and do not select the s3 endpoint.
After Creating a vpc , It will look a lot like this with all the resource map.

After the Vpc is created the next step is to create an Auto scaling group, But for that we need to create a launch template as well.
Create a launch template by selecting the OS version you want, select the key pair, Also create a new Security group and allow ssh and custom TCP port 8000 for IP anywhere.
Now click on Create a launch template and Attach it to the auto-scaling group, Reason to do so is if in the future the load increases and there is a need to increase an instance then the auto-scaling group will take reference from this Template and then launch an instance of the similar configuration.

Reminder! Always select the same vpc which is created as above and the ec2 instance should be launched in the private subnet in the availability zones. Select the private subnet us-east-1 -private and similarly second one also, Also select the keypair in .pem form
Do not attach any load balancer now. Keep it for later, Specify the size of the auto-scaling group "Desired-Size=2" "Minimum-size=1" and "Maximum-size=4" You can set this as per your requirements.
Now let's go to the Instances and see if that auto-scaling group has created 2 instance for us, As mentioned above in the desired capacity.

Both instances are created in the private IP in the Availability zone.
After this we are much closer to completing the project, So here in Layman's term. What we have to do is access the instance in the Private subnet with the help of public subnet through a medium/mediator called as Bastion-Host/Jump-host.
The steps to create a bastion host is similar just create an instance and the thing to remember is in the network setting gives the same vpc as above. Select allow ssh, and allow auto-assign public ip = enable and subnet select the public subnet their subnet-public1-us-east1.

Now what we have to do here is ssh the bastion host and from the bastion host ssh the instance in the private subnet.
Now connect to the bastion-host and then to launch the private instance we require a key, which we created while creating the 2 instances, But now in my case as I was using putty instead of the local terminal. So when I logged into the bastion host, what I did is I created a vim file.
#vim ubuntu-key.pem (and copied the key pair here in this vim file and then gave the key pair permissions as
#chmod 400 ubuntu-key.pem (key pair name)
Now I did the #scp -i ubuntu-key.pem "ubuntu-key.pem" ubuntu@10.0.153.162:/home/ubuntu
After this Just do #ls to see the key is copied successfully.
Just where I have written "ubuntu-key.pem" add your specific key name there.

Now after the above steps to copy and scp here for logging the step is #ssh -i key name ubuntu@10.0.153.162 ( this is the private Ip as we are connecting through ssh with the private IP)
The next thing to do here after successfully logging is to create an #vim index.html file and add certain code or content to display it to the web server.

Copy any html and css code and paste it.
Run the application through http-server through a certain port
python3 -m http.server 8000. (This is because as in step5 we have given custom tcp and open port 8000)
Now to manage the traffic what we have to do is balance the load or the flow of traffic it will be done through a load balancer and attach this instance as a target group to the load balancer
Now go to the load balancer It should be in the public subnet and have access to the internet or internet facing.
The first step is to create a target group in the load-balancer, name the target group and then select the instance attached to the tg and then select the vpc as created above and select "include as pending" and allot the port number 8000 there now create the load balancer the application load balancer and name it as you want select the default vpc as above and the security group in which you have allowed TCP 8000, select both of the public subnets


Creating load balancer .
Now keep the listener port as 80

Now after configuring the load balancer as it is provisioned try to access it will show the error as in the above image, This error is because we have only given access to the ssh and tcp 8000 in the security group of this instance. So now give access to the port 80 in security --> edit inbound rules and allow port 80 as well (As port 80 is allotted for the http server to access the website and make it live to the internet)

And Now try to access it through the dns

While accessing the Dns make sure that the "python3 -m http. server 8000" cmd is running and the instance is on and working other wise it will show error 502 Bad Gateway

Copy the DNS and paste it to the Chrome you can see that the html code in the index.html file in the instance is live and you have completed the vpc configuring demonstration and hosted and application.

The application is live.
So now there's an application running in a single instance and now if you want to understand the concept of the application load balancer, Utilize the second instance as well and run it through the Bastion-Host and then follow the above commands as following mentioned in step 15,16,17,18,19.
Now as you will run the application in second instance and refresh the load balancer and copy the dns and run it.
IT will show different websites at every refresh time , so why it happens? It is because the (ALB application load Balancer)works on the round robin algorithm that is If 2 instance it will work as.....
1-->2-->1-->2.
*SHORT DESCRIPTION OF DIFFERENT AWS RESOURCES USED:
-->𝐀𝐮𝐭𝐨-𝐒𝐜𝐚𝐥𝐢𝐧𝐠-𝐆𝐫𝐨𝐮𝐩𝐬 == By integrating Auto-scaling groups we can achieve➤Dynamic scaling ➤High availabilty ➤efficient resource managment ➤the network isolation and security.
-->𝐍𝐀𝐓-𝐠𝐚𝐭𝐞𝐰𝐚𝐲𝐬 == Enables the instances in private subnets to access the internet.
-->𝐈𝐧𝐭𝐞𝐫𝐧𝐞𝐭-𝐠𝐚𝐭𝐞𝐰𝐚𝐲 == It provides a secure and controlled point of access for resources within vpc to connect and to communicate with the public internet.
-->𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐆𝐫𝐨𝐮𝐩𝐬 == Presents at private subnets which allows the specific request to application.
-->𝐋𝐨𝐚𝐝-𝐁𝐚𝐥𝐚𝐧𝐜𝐞𝐫 == It distributes incoming traffic across multiple instances, ensuring➤fault tolerance ➤maximizing resources utlization.
Aws Documentation link for Public and Private subnet VPC: https://docs.aws.amazon.com/vpc/latest/userguide/vpc-example-private-subnets-nat.html
Thanks to the Guidance of Abhishek Veeramalla which helped me to demonstrate this project.